
PowerShell is a powerful interactive command-line interface and scripting environment included in the Windows operating system. Adversaries can use PowerShell to perform a number of actions, including discovery of information and execution of code.
PowerShell may also be used to download and run executables from the Internet, which can be executed from disk or in memory without touching disk.
We have a separate blog which touches certain aspects of a malicious PowerShell script here - Decoding Malicious PowerShell Activity - A Case Study - Blog - Malware Questions - Sophos Community
A number of PowerShell-based offensive testing tools are available, including Empire, PowerSploit, PoshC2, and PSAttack.
On the host side of forensics, there are various places where we look for signs of suspicious PowerShell script or command execution whether it’s local or remote.

Event ID 7045: Adversaries often attempt to register backdoors as Windows Services as a persistence mechanism i.e. survive reboots.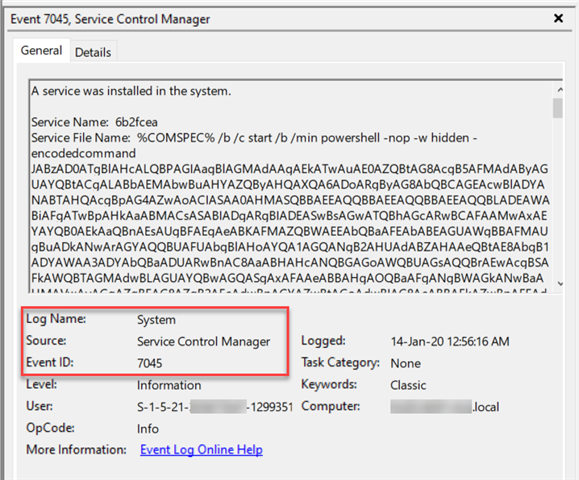
Event ID 400: The engine status is changed from None to Available. This event indicates the start of a PowerShell activity, whether local or remote.The field ‘HostApplication’ might display the encoded bits used such as:
powershell.exe -EncodedCommand VwByAGkAdABlAC0ASABvAHMAdAAgAC0ATwBiAGoAZQBjAHQAIAAiAEgAZQBsAGwAbwAsACAAdwBvAHIAbA BkACEAIgA7AA==
Event ID 600: indicates that providers such as WSMan start to perform a PowerShell activity on the system, for example, “Provider WSMan Is Started”.Event ID 403: The engine status is changed from Available to Stopped. This event records the completion of a PowerShell activity.<aside> 💡
This is not applicable for PowerShell 2.0
</aside>